STEALTHCRYPTO

Hello friend. If you are interested in joining the STEALTHCRYPTO project, it's worth reading the reviews that will help you get information that can help you when looking at their vision and mission of the STEALTHCRYPTO project:
Business Model
StealthCrypto has the experience and the expertise to protect your data using next-generation decentralized blockchain security technology to help defend against emerging challenges in an evolving threat landscape. Our high-performance network encryption for long-term data protection Quantum key generation and quantum key distribution
StealthCrypto makes cloud storage, IoT , and communications secure, and faster with StealthCrypto’s patented StealthCrypto
What is StealthCrypto?
The
StealthCrypto™ utility token will be the native cryptocurrency of the
StealthCrypto™ system. Funds collected through the token sale will be
used to develop as well as activate and purchase StealthCrypto Cloud™
products and products in the StealthCrypto™ ecosystem. The values of
StealthCrypto™ tokens are fully dependent upon the developments of
Stealth Grid™ and market demand.
Data at Rest & in Motion
StealthCrypto™
keeps data dynamically secure by using dynamic split encryption,
dynamic split geo distribution, and a dynamic split encrypted
authentication process that authenticates users according to client
policies which govern level of access. Data is highly vulnerable to
outside threats, and not a day goes by when yet another supposedly
protected system is hacked and valuable information is stolen.
StealthCrypto™ ensures that data is only available to authenticated
parties, locking out cybercriminals and better protecting people, places
and things.
Flexibility
StealthCrypto™
can be used with embedded private keys on devices and end-points,
and/or with no requirement for secure local storage, or on the
StealthCrypto Cloud™ NAS Server and mobile devices.
Benefits
StealthCrypto™
Trust Centers™ (TC’s), or NAS systems, offer a true peer-to-peer
communication and data storage that can be embedded on a chip and can be
configured for cross-domain secure communication, between stand-alone
Trust Centers or StealthCrypto™ Cloud NAS servers. In this way, it’s
social by design. Stealth Grid™ products and solutions are based on the
underlying thought of creating an eco-system of safe interaction for
consumers as well as business customers. Business opportunities today
are diverse. Stealth Grid™ intends to be positioned as a pioneer, a
global influencer, and a thought leader regarding blockchain usage for
cyber-security purposes
Mobile Communications/Blockchain
Mobile
and blockchain developers can deploy StealthCrypto™ to secure
authentication and key exchange requirements. Its certificate-less
feature and peer-to-peer functionality make it a perfect security
ingredient for e-banking solutions and so much more.
Enterprise/Government Communications (email, VOIP, FTP, Collaboration)
Working
closely with another partner, StealthCrypto™ is developing its
technology on micro SD cards, creating an offering capable of securing
any communications device (fixed or mobile). This quantum resistant
service can replace TLS/SSL and SSH and facilitate secure email, VoIP,
authentication, blockchain and file sharing applications along with
Smart City platforms.
Security Software as a Service (SaaS)
The
combination of StealthCrypto™ protected apps that use a downloadable
software secure element solves the SMB security challenge without the
need and cost of deploying hardware secure elements

Stealth Crypto™ Quantum Mesh Network Insurance
Qubit
Blockchain will take a small percentage in every transaction that will
be held in a pool that will hedge against negative events. There will be
incentive base insurance platform for buying insurance from mesh
network to get paid in case a negative event occurs. We will be the
Global Crypto Insurance Reserve (GCIR) platform with a smart contract
that can be unlocked by the insured — if the event in question did
occur, or by GCIR.
Creating the StealthCrypto Phone
Stealth
Grid™ is the developer of the StealthCrypto Phone™, an ultra-secure
mobile phone that is the first open source blockchain smartphone and NAS
Units. The smartphone features hard kill switches, empowering its users
to take back control of their privacy. All phones feature a built-in
privacy control center giving users full access and function control on
their phone. Smartphones were never designed with security or privacy as
a major factor, though these are essential to ensure the trust of the
blockchain network. As technologies such as cryptocurrency mining,
trading, and online payments become available for these devices, they
turn into even more valuable targets for malicious actors. Many apps
that we download harvest data by asking for more permission types than
are really needed (for example, flashlight apps that need access to your
contacts) and so jeopardize our privacy. Nowadays, smartphones are just
as vulnerable to hackers and malware as PCs, but are even harder to
protect. Another p Another problem with modern smartphones is that they
have so many capabilities. Thanks to a hypercompetitive marketplace,
there is a constant race to add more and more features. This has two
implications: 1) security often lags behind, and the potential attack
security often lags behind, and 2) the potential attack surface is
enormous. It is relatively easy for a determined attacker to hack a
device, access it and obtain data. There have been several attempts to
tighten up smartphone security — like the introduction of end-to-end
encryption on some widely-used messaging apps such as WhatsApp and
WeChat. But unfortunately, this is not enough. While an app may be
secure, this does not help if you have already been tricked into
downloading a piece of malware that sends screen captures of your
messages or records your calls. To prevent such attacks, smartphones
must be secured not only against external intrusions, but also at the
hardware low-level of the phone itself. This can only be achieved by
tightening the operating system, which means that a phone must be
developed with security in its entirety, as the necessary level of
protection cannot be achieved through app development alone. These
considerations have forced manufacturers of secure mobile phones to
develop phones which are both expensive to produce and provide limited
usability in favor of security, therefore leaving no room for advanced
features.
The
StealthCrypto™ Phone™ contains a platform that will allow the user to
physically disconnect the battery, Wi-Fi antennas, Bluetooth and
geolocation, the camera and microphone, etc. It also will not allow the
phone to connect to a Stingray or any other IMSI catcher device. The
StealthC The StealthCrypto™ Phone is creating a new paradigm for
wireless networking: StealthCrypto™, an autonomous, decentralized mesh
network. Mesh networks technology is helping to enable the 4th
generation of wireless mobility by using basic radio frequency (rF)
physics in a new way — overcoming inherent limitations to achieve
unprecedented coverage, throughput, flexibility, and cost-efficiency.
Mesh networking offers a new model of seamless mobility that’s already
transforming wireless data and voice communications for citizens, on the
battlefield, in police work, at the scene of fires, and in other
settings where instant, wireless information access can provide both
economic, quality of life, and safety benefits.
Our StealthCrypto Cloud apps are addicted to the backbone:
• Hardened android operating system with granular security management and streamlined, security-optimized components
• Permission enforcement module controls access to network, data and sensors, keeping you in control of your security policies
•
Baseband firewall protects against over-the-air attacks with constant
monitoring of baseband processor activity, baseband attack detection,
and automated initiation of countermeasures
• Two-layer storage dynamic split encryption system protects data at rest against unauthorized access
• Biometric technology security enabled by fingerprint recognition and iris scan
• Secure encrypted messaging through Private StealthCrypto™
• Documents, photos and videos transferred securely over Private StealthCrypto™
• Secure, encrypted voice and video calling
• StealthCrypto wallet, safe and secure
StealthCrypto Decentralized App-Store
Most
users retrieve the apps they use through an app store, managed by the
OS vendor of their device. These stores provide users with little value,
mostly in the form of auditing and reviewing apps ensuring better
protection of the users from malware, at a high cost: stores charge
roughly 30% of the developer’s proceeds, including most forms of in-app
payments, out of developers’ pockets. Most estimates put the combined
revenues of Apple and Google app stores in recent years at between
$50-$100 billion annually. But the damage But the damage to users is
even higher. The operators of the app stores use their monopolistic
power to impose censorship on the app offering: from barring apps that
contain unapproved content (such as gambling or adult content apps), to
bolder limitations on apps that pose a risk to the operator’s business
(for example, Apple blocked all blockchain wallets for the lion’s part
of 2014). The Stealth Grid™ D-App S The Stealth Grid™ D-App Store is a
decentralized and tested app store for any type of app on the
StealthCrypto™ platform, in which users pay developers 100% of their
subscription fees directly. Auditing services providing security
protection, parental control, etc. may be provided by trusted 3rd
parties and sold directly to the subscriber
STEALTHCRYPTO SYSTEM
The StealthCrypto Token is essential to the function of the StealthCrypto Ecosystem. StealthCrypto is a functional Token that will be used on the platform to access various features, products and fees. Furthermore, as StealthCrypto services and products become more liquid and valuable over time, we anticipate it could be used to rebalance individual portfolios. In other words, liquidity generated by StealthCrypto can enable users to shift allocations between various currencies quickly and easily.

TOKEN SALE "QMN"
Total token supply: 400,000,000
200,000,000 tokens for Stage 1 Token Crowdsale
Pre Tokens Sale to start on January 28, 2018. The initial token price (ICO) will be set at a minimum of S0 .50, or present market value above S0 .50, when ICO launches July 05, 2018. 200,000,000 tokens will be reserved for Stage 2 Token Crowdsale (50% of total).
Stage 2 will happen no sooner than 2020, and all tokens will be sold at market price, not at a fixed $0 .50 USO value (important note: all percentage below will be adjusted in accordance with actual amount raised, e.g. if we sell 70M of 1 00M tokens, the following numbers will be multiplied by 0.007)
STEALTHCRYPTO FUND-20O,OOO,OOO STEALTHCRYPTO
The StealthCrypto Fund operates as part of our business model, ensuring a stable token with a bright future. It is in our best interests to ensure that the STEALTHCRYPTO™ purchasing power grows over time and market manipulation is avoided. A total of 400 million tokens will be issued. This is how it breaks down in dollars during planning - the actual price is subject to change:
STEALTHCRYPTO ALLOCATION
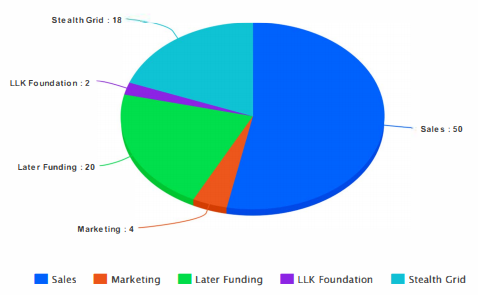
To contribute and Know the progress of this offer, you may visit some of the following Links:
Website: https://www.stealthcrypto.io/
Whitepaper: https://www.stealthcrypto.io/assets/images/pdf/whitepaper.pdf?pdf=Download-Whitepaper
Telegram: https://t.me/stealthcrypto2018
Facebook: https://www.facebook.com/StealthCrypto-143787762986167/
Twitter: https://twitter.com/stealthcrypto_
Reddit: https://www.reddit.com/r/stealthcrypto/
Bounty thread: https://bitcointalk.org/index.php?topic=4477499.0
author:
rivaldo2020
BTT Profil link:
https://bitcointalk.org/index.php?action=profile;u=2051385
0x320f6344D4BE878C96e77AD580e2EE132C4BF6F8

No comments:
Post a Comment